Although the L2TP/IPsec VPN protocols were primarily developed by Microsoft and Cisco, there are open source alternatives that work well in Linux. L2TP/IPsec is an older VPN protocol but it is still quite popular despite the Snowden revelations that the NSA may have deliberately weakened the protocol. It supports various encryption ciphers and is built-in to Microsoft Windows and many routers.
If you want to use L2TP/IPsec on Linux you are probably going to need to install a few extra packages. I wrote this tutorial on Linux Mint 17.3 Cinnamon desktop edition, but it should be very similar for other flavors of Linux, and I will discuss these as well. Plenty of screenshots are included below.
L2TP/IPsec Linux setup
Step 1: Install required software
The following software firstly needs to be installed on your Linux machine:
1) NetworkManager
Most Linux users are going to need to install a couple of packages that probably do not come with your base install. Network management used to be a pain on Linux. Every distribution and often different versions of the same distribution had varying ways of managing network profiles. Fortunately, The GNOME Project has released a project they call NetworkManager that greatly simplifies network management on Linux and works on most desktops and even on the command line, if you are so inclined.
For Linux Mint Cinnamon users, NetworkManager comes with your base install and is the familiar Network manager applet that is probably already on your panel. If you are using another Debian derivative, such as Ubuntu, you probably already have NetworkManager installed as well. The same goes for Red Hat derivatives like Fedora or CentOS.
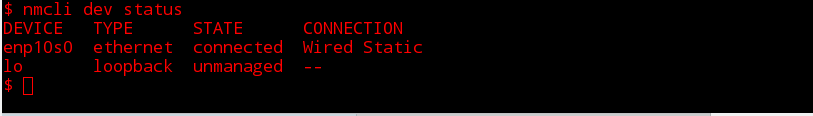
You can use the command line tool to check what devices are managed by NetworkManager;
$ nmcli dev status
DEVICE TYPE STATE CONNECTION
enp10s0 ethernet connected Wired Static
lo loopback unmanaged --
$
For all distributions you should be able to search your package repositories and find and install the NetworkManager package if your are not already using it.
2) Layer 2 Tunneling Protocol (L2TP)
L2TP is a tunneling protocol that offers no encryption but as the name suggests, is an important component of the L2TP/IPsec VPN protocol. Despite being developed mainly by governmental and corporate interests, L2TP is an open protocol standard.
There are a couple of different L2TP open source implementations but xl2tpd can be found in most extra repositories. The community repository for Arch, the EPEL for Red Hat based and in the main repositories for Debian based.
So, if you are on Linux Mint Cinnamon, go ahead and open up your Software Manager and search for “xl2tpd“:
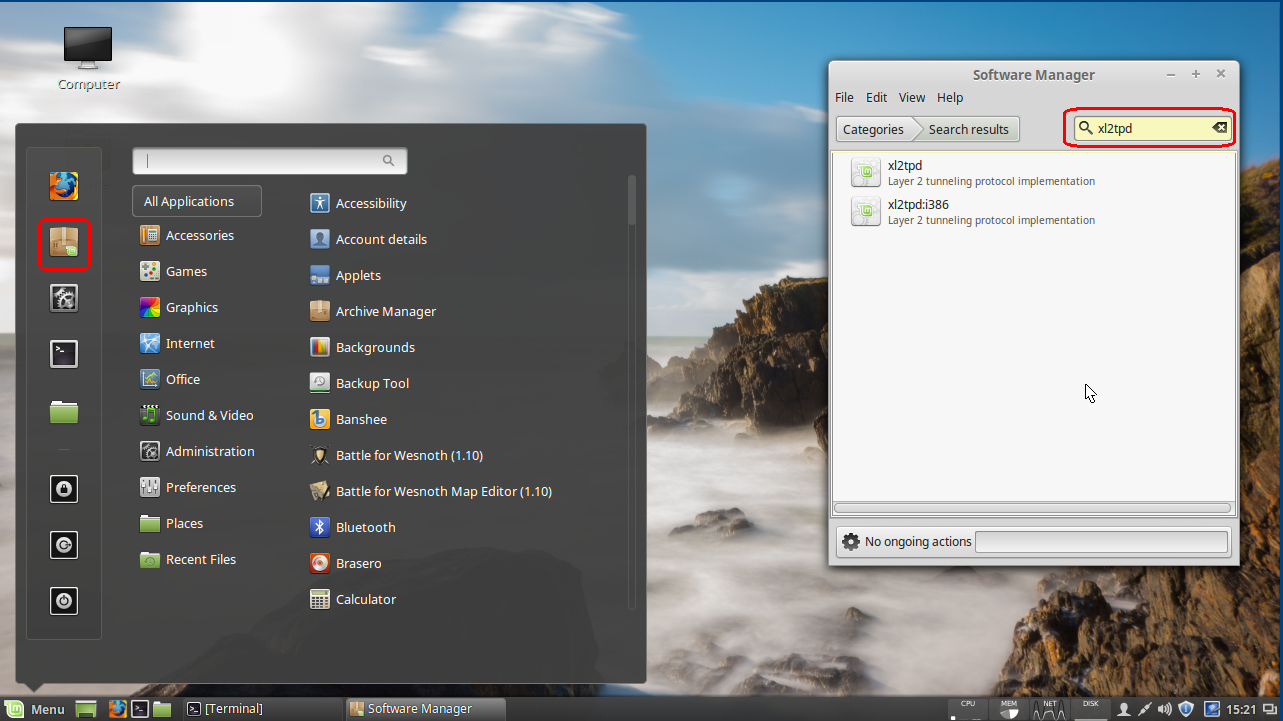
If you are running a 64 bit OS double-click the xl2tpd otherwise select the i386 version.
Click the Install button to install the package:
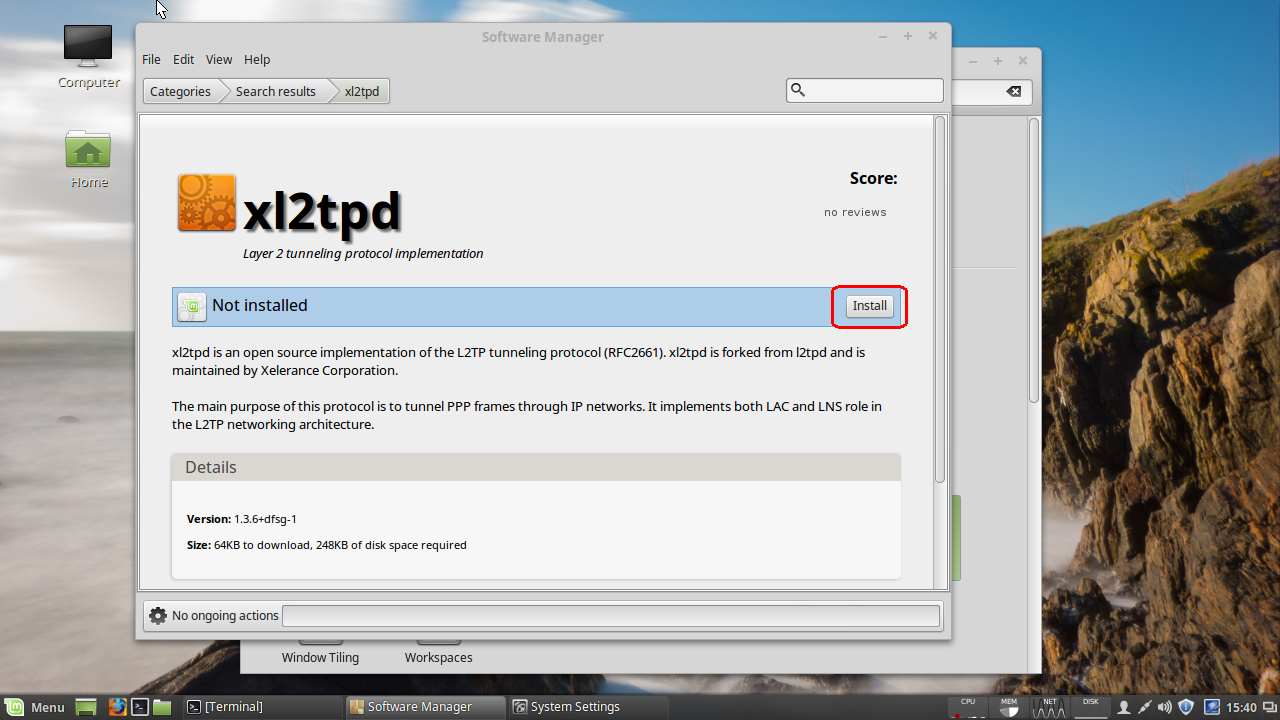
So, now we have the L2TP part but we still have another package to install.
3) Install IPsec
IPsec is the IP protocol suite that handles the authentication and encryption in a L2TP/IPsec VPN. This is also an open standard with open source implementations.
A popular open source Linux implementation of IPsec is strongSwan and packages can be found in many popular distribution repositories.
Openswan used to be the IPsec project of choice but has been deprecated in Debian and descendants. However, if strongSwan doesn’t work out for you, you might want to give Openswan a go.
Arch users will need to install from the AUR, while Red Hat and Debian variants should be able to install the package from the base repositories.
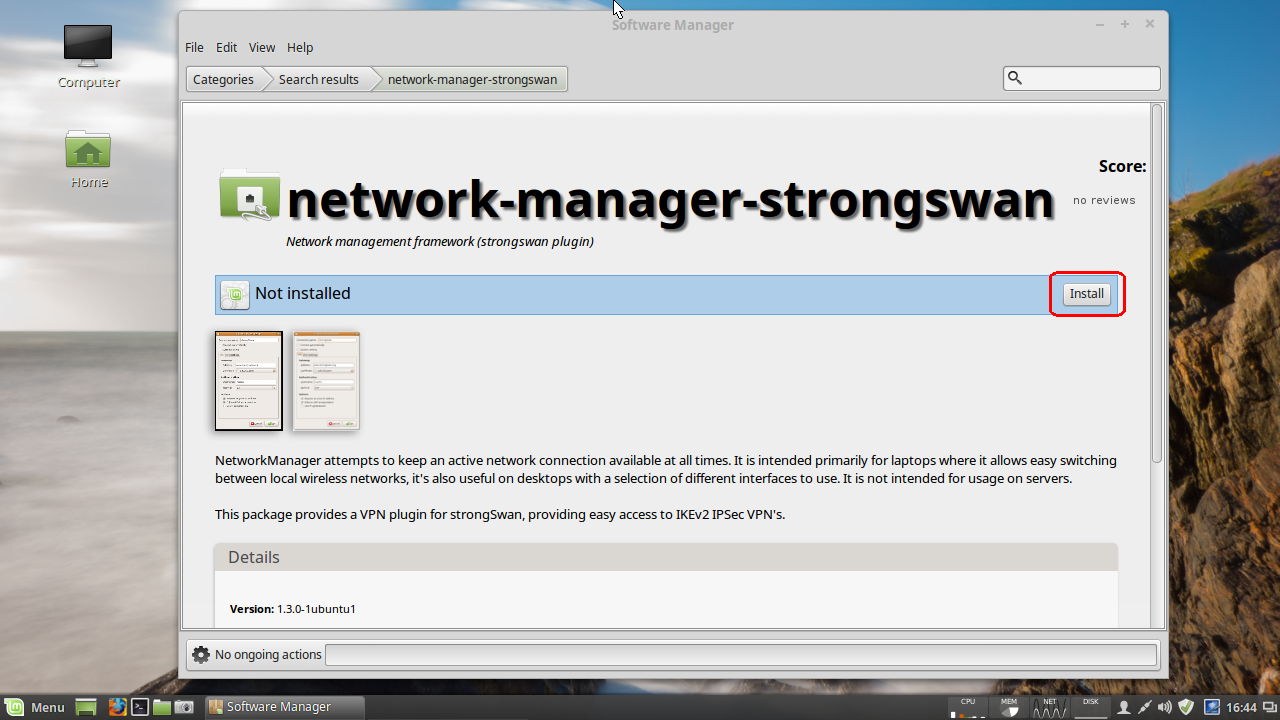
On Linux Mint, open up the Software Manager and search for strongSwan.
Since you are going to want the NetworkManager plugin, select the package network-manager-strongSwan which will install the strongSwan libraries an required plugins as a dependencies.
Step 2: Create connection
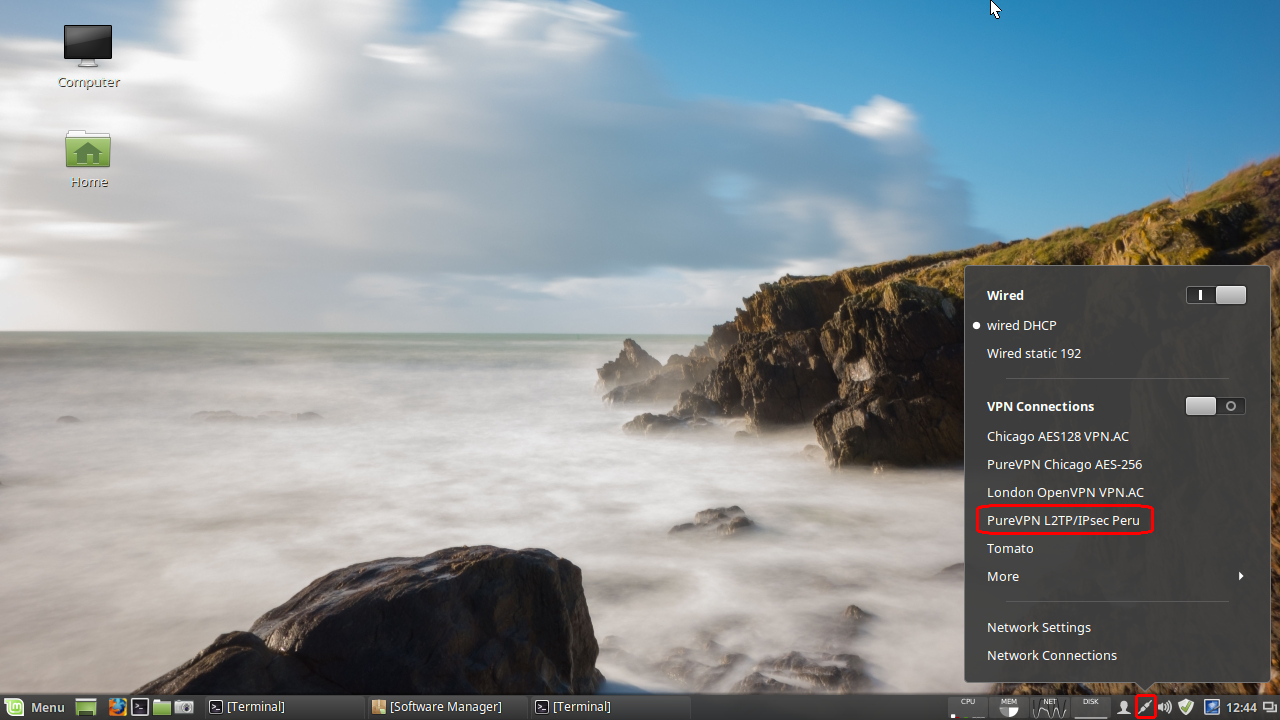
Click on network manager applet and then click on Network Connections:
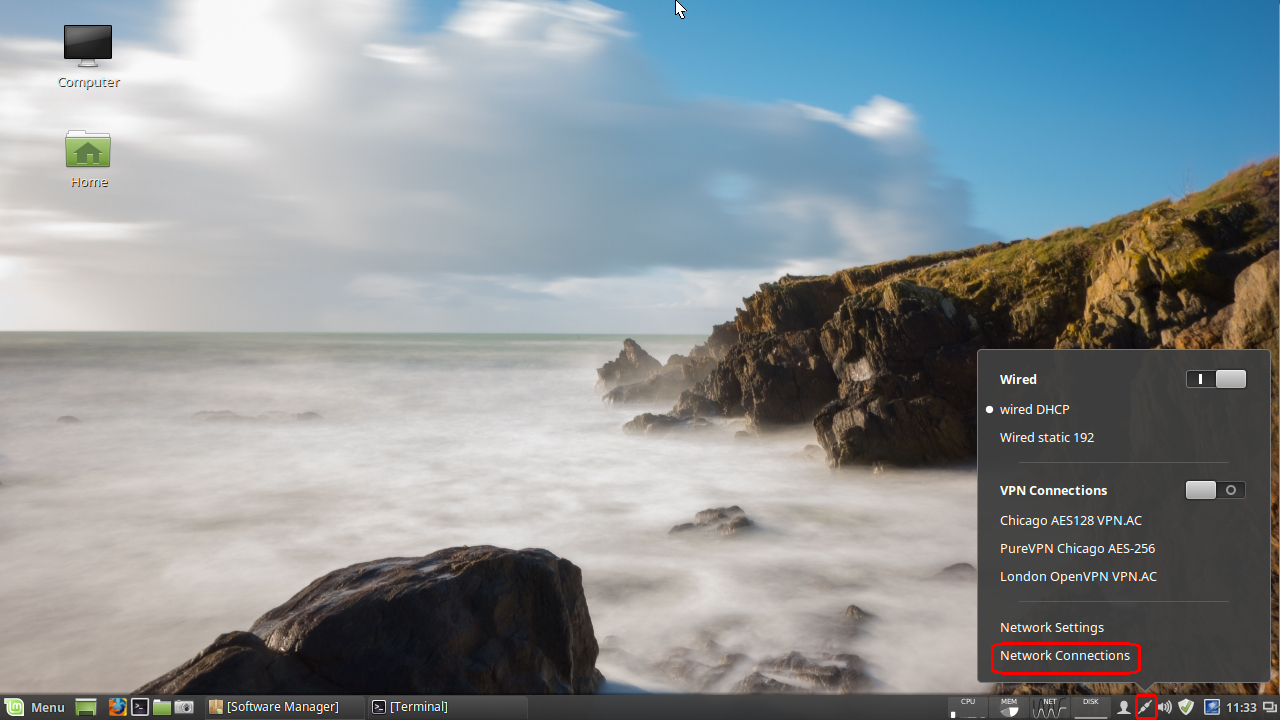
Click the Add button in the window that pops up:
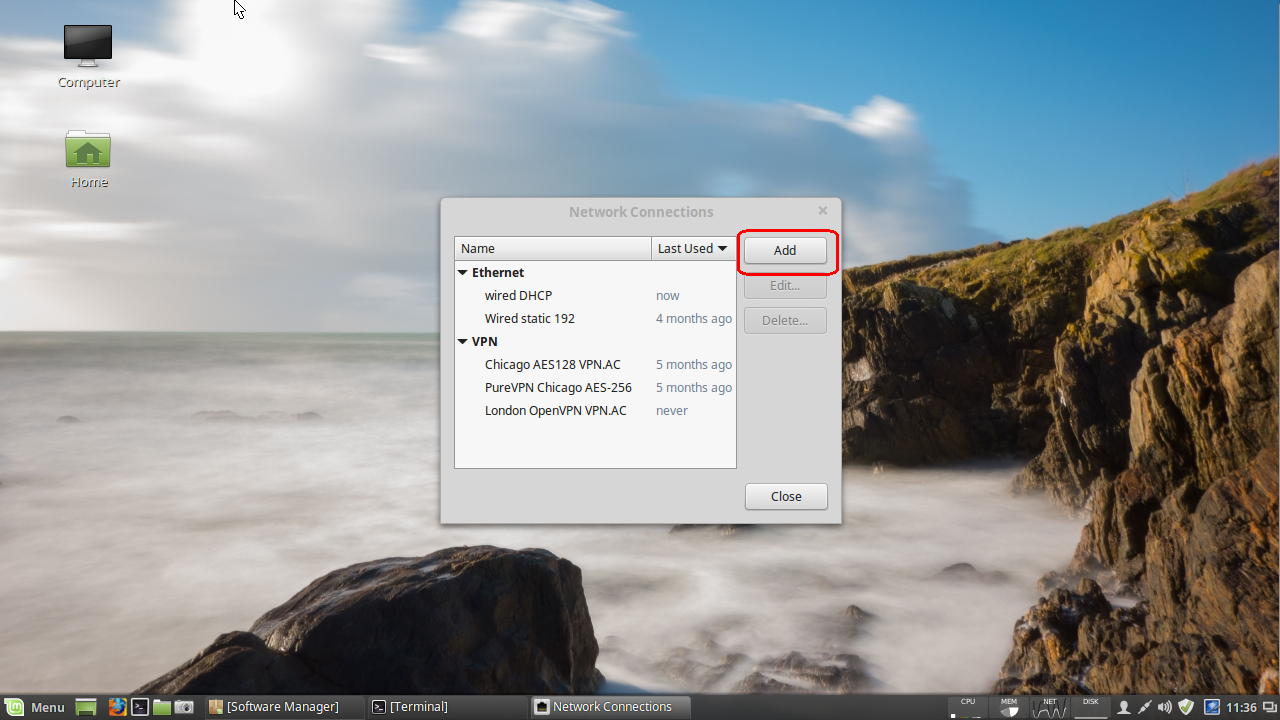
This brings up a Choose Connection Type dialog. Click the pulldown menu and select IPsec/IKEv2 (strongswan) option under the VPN section:
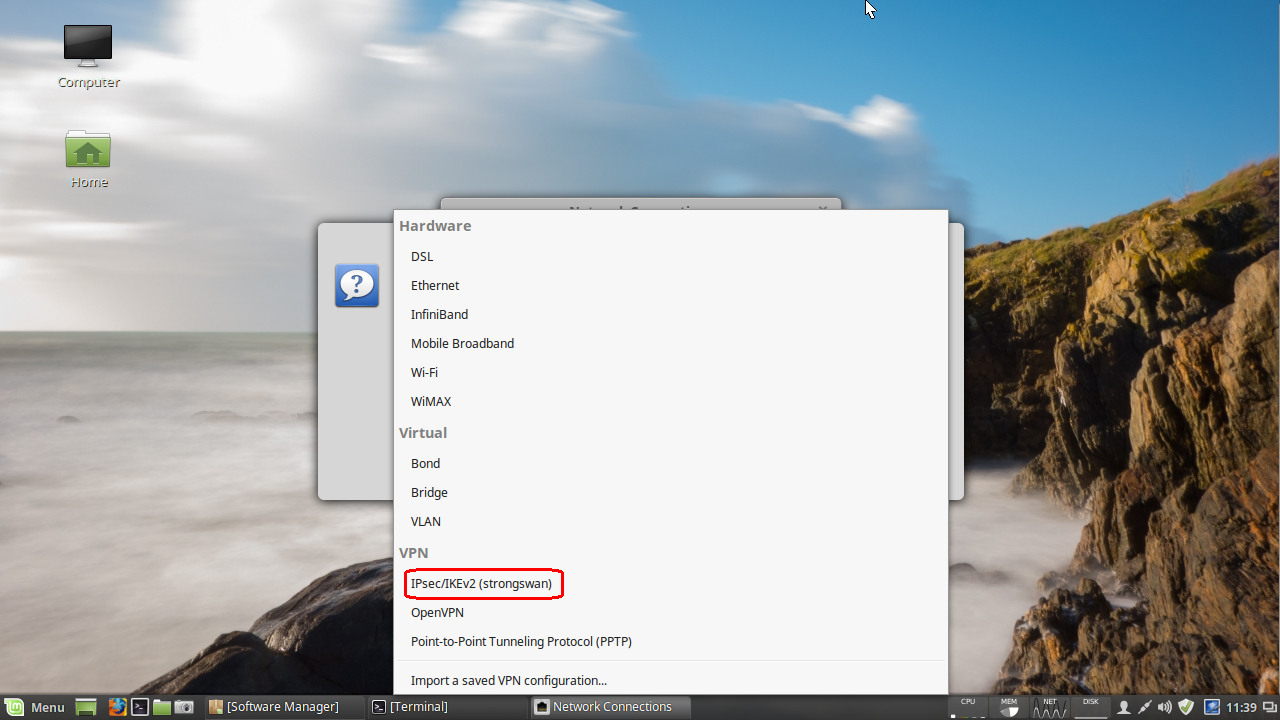
Click the Create… button (this will bring up a new dialog).
Enter VPN connection details
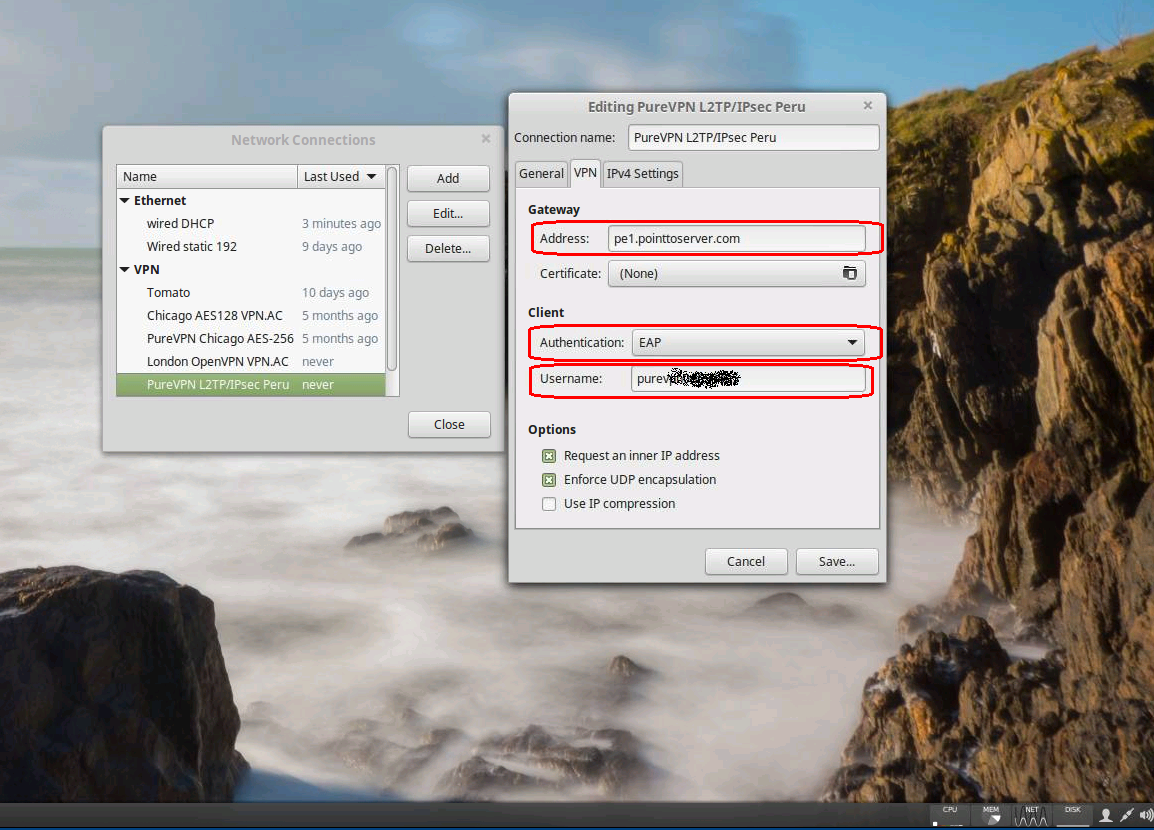
- For the Connection name field, enter a memorable name for your connection.
- Under Gateway, fill in the Address field with the value of your VPN provider’s L2TP/IPsec server.
- Under Client, click on the Authentication pull-down menu and select EAP.
- Under Username, enter your username provided by your VPN service.
PSK is supported starting with NetworkManager-strongswan-1.3.1, but strong secrets are enforced.
My current release of Mint is using 1.3.0 and I had to download 1.3.1 from the latest Ubuntu package repository and install it manually. I would imagine that this will be rolled out to Mint’s repositories very soon.
Checking the strongSwan NM code, they have defined “strong secrets” as a key length of 20 characters or longer. If you need a PSK you will want to select Pre-shared key under the Authentication: pull-down menu rather than EAP.
You may also need to check any or all of the Options check boxes depending on your VPN servers configuration.
When you are finished click the Save… button.
Now you can click on the NetworkManager applet and select your newly configured connection:
Depending on your authentication method you might get a dialog asking for your VPN password and will be given the options to save your password for future use.
Once your VPN is established you should receive a pop-up status message and the NetworkManager applet will change to have a little lock on it:

As always, you should double-check that your IP reports as your VPN server’s and not your real IP.
I hope this walkthrough helps you set up an L2TP/IPsec VPN on your Linux box! Feel free to leave your questions and suggestions in the comments section below.

Is there a way to reduce the minimum 20 character PSK limit?
You may want to install the PPA for the NetworkManager L2TP plugin.
The following blog post is what I used to solve my issue, as well as specifying a less secure protocol because NetworkManager doesn’t attempt 3des-sha1-modp1024 anymore by default.
http://blog.z-proj.com/enabling-l2tp-over-ipsec-on-ubuntu-16-04/
In case somebody come across this post, here is my specific case and solution https://forums.linuxmint.com/viewtopic.php?f=90&t=237036&p=1308120#p1308120
Pre-shared key option is missing in mint 17.3 too… I’m wondering how You did the tutorial since we have the same version…
with Mint 18 KDE it doesn’t work, Pre-Shared option missing
Thanks a lot for the tuto, this is the best solution I’ve found to add L2TP/IPSec in my Mint 18 Cinnamon.
And thanks to Ernest Bowie : version 1.4 is working great for me, 1.3.1 didn’t (no “IPsec/IKEv2 (strongswan)” in the pulldown menu).
There is a compatibility issue with the latest network manager in Mint 18 and the network-manager-strongswan package. You need version package version 1.4.0 or higher, but 1.3.1 is what comes in the default repos. To work around this until they update the repo you can do the steps from above and then install the 1.4.0 package from the deb file found here: https://launchpad.net/~raharper/+archive/ubuntu/bugfixes/+build/10771765/+files/network-manager-strongswan_1.4.0_amd64.deb
This worked for me, but I cannot save the VPN configuration if I select the “Pre-shared key” – the Save button is grayed out.
Any hints?
Hi, same here. Using Mint 18 Cinnamon.
Read the tooltip when you hover over the password field. PSKs are required to be at least 20 characters.
It seems that it’s only possible to put either the PSK or the user password but not both as required by PSK.
How about a package for 32-bit too?
Hi, same here. Using Mint 18 MATE.
Any hints?
Hi, after doing step1, I can’t select “IPsec/IKEv2 (strongswan) ” from the pulldown menu.
I Installed xl2tpd, and network-manager-strongSwan.
Using Mint 18.
Any idea what it could be?
I have this same issue. Have been searching the web for solutions, but so far no luck.
Same here :(
Try installing NetworkManager-strongswan-gnome if you haven’t already. That’s what I needed to do in Fedora.